 Last updated 1 year ago
Last updated 1 year agoIn this article, will will cover how to sniff serial port communication with the help of virtual COM ports.
Serial port sniffing is the process of intercepting the data being transmitted over a serial communication port. It can be useful for a variety of reasons, including troubleshooting, debugging, or reverse engineering. Serial ports are commonly used to connect devices such as modems, printers, and industrial control equipment to a computer.
⚠️ Please be aware that serial port sniffing should only be performed with proper authorization.
First of all, you need to know the exact physical COM port number on your computer. Start by going to the Device Manager. Once there, expand Ports (COM & LPT). Keep the COM port assigned to the device by Windows, such as COM1, COM2, COM3, etc.
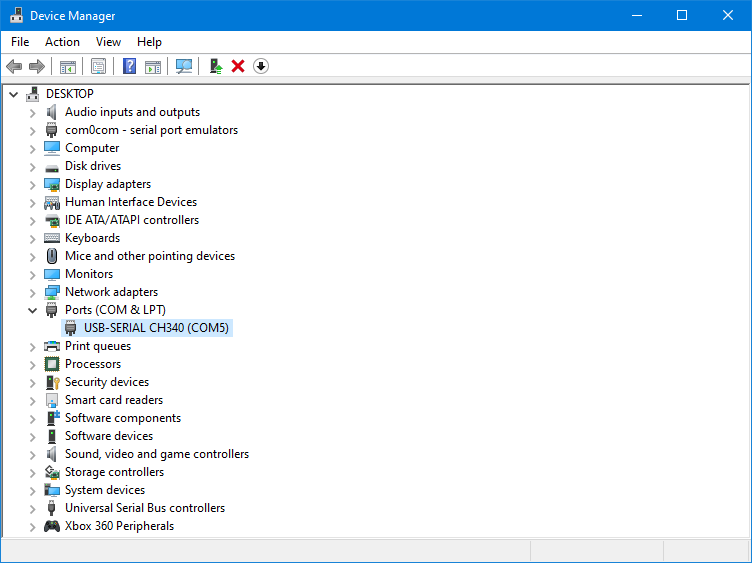
In this example, my physical port is COM5.
Let's say I have a piece of software which is communicating with COM5 and I want to "sniff" that traffic. However, sniffing COM5 traffic directly is not possible. So we will create virtual ports.
In order to sniff serial port communication, we need to create virtual COM ports.
A virtual COM port is a software-based interface that emulates a physical serial communication port on a computer. It allows software applications to communicate with hardware devices that use a serial interface without the need for a physical serial port. A virtual COM port is assigned a COM port number, just like a physical serial port. Software applications can communicate with the virtual COM port using standard serial communication protocols such as RS-232, RS-485, or TTL.
Null-modem emulator (com0com) is an open source kernel-mode virtual serial port driver for Windows, available freely under GPL license.
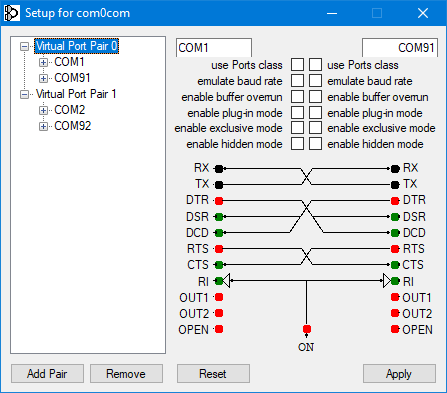
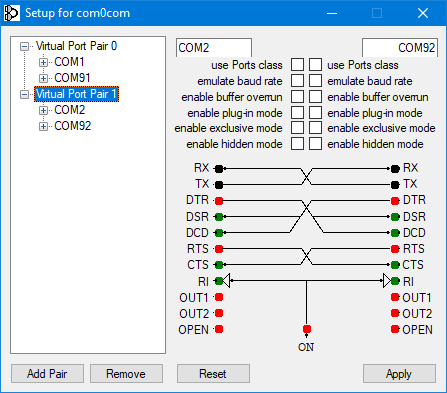
You must use your own physical COM port number by checking from Device Manager.
You can change your virtual port numbers as you wish, or stick to the numbers I randomly selected. Ensure that the ports you selected are available and not in use.
Now that our virtual ports are active, we can route physical port communication as we want. We will use hub4com for directing COM port traffic.
Before routing the traffic, our physical port (COM5) must be available. So, we need to close the application which uses our physical COM port.
Press Enter
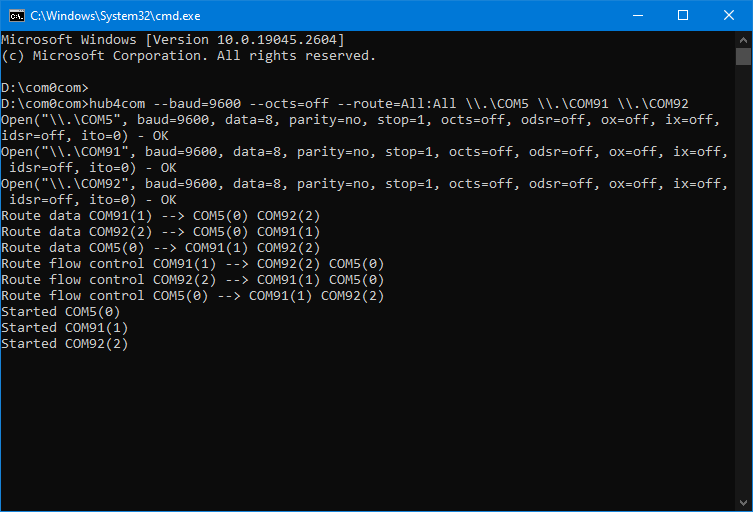
⭐ The hub4com command prompt must be running during sniffing.
Now that the physical port traffic is routed, we can now open the software which was using the physical port. But this time, it must use one of the virtual ports (COM1), instead of physical port (COM5).
We can now sniff serial port communication with the help of Vovsoft Serial Port Monitor. The sniffer software must use the other virtual port (COM2).
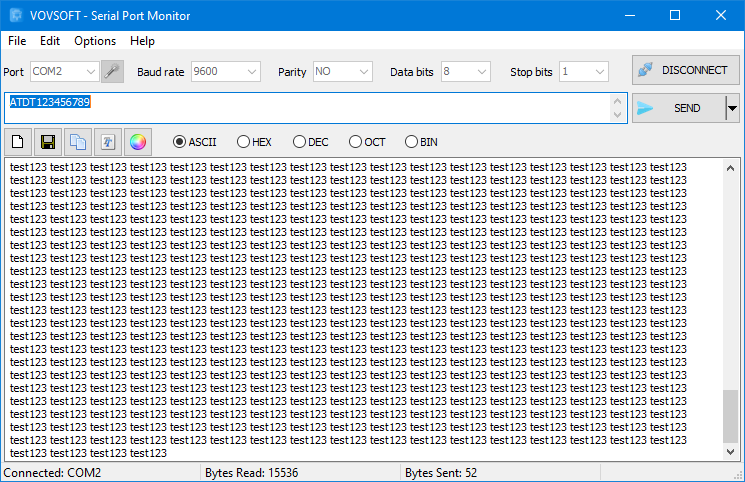
As a result, we can see all incoming and outgoing data (via COM1) in the sniffer program (using COM2). In addition, we can send data through the sniffer program, as if it were sent from the other program.

 Responses (1)
Responses (1)